
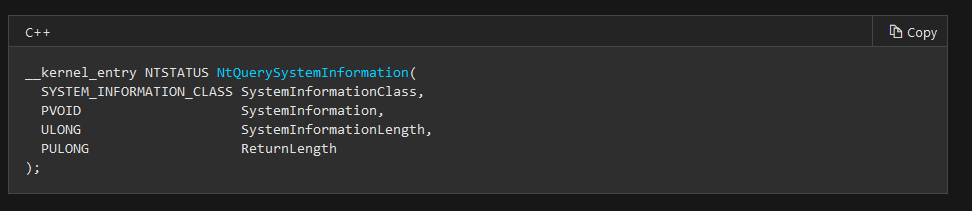
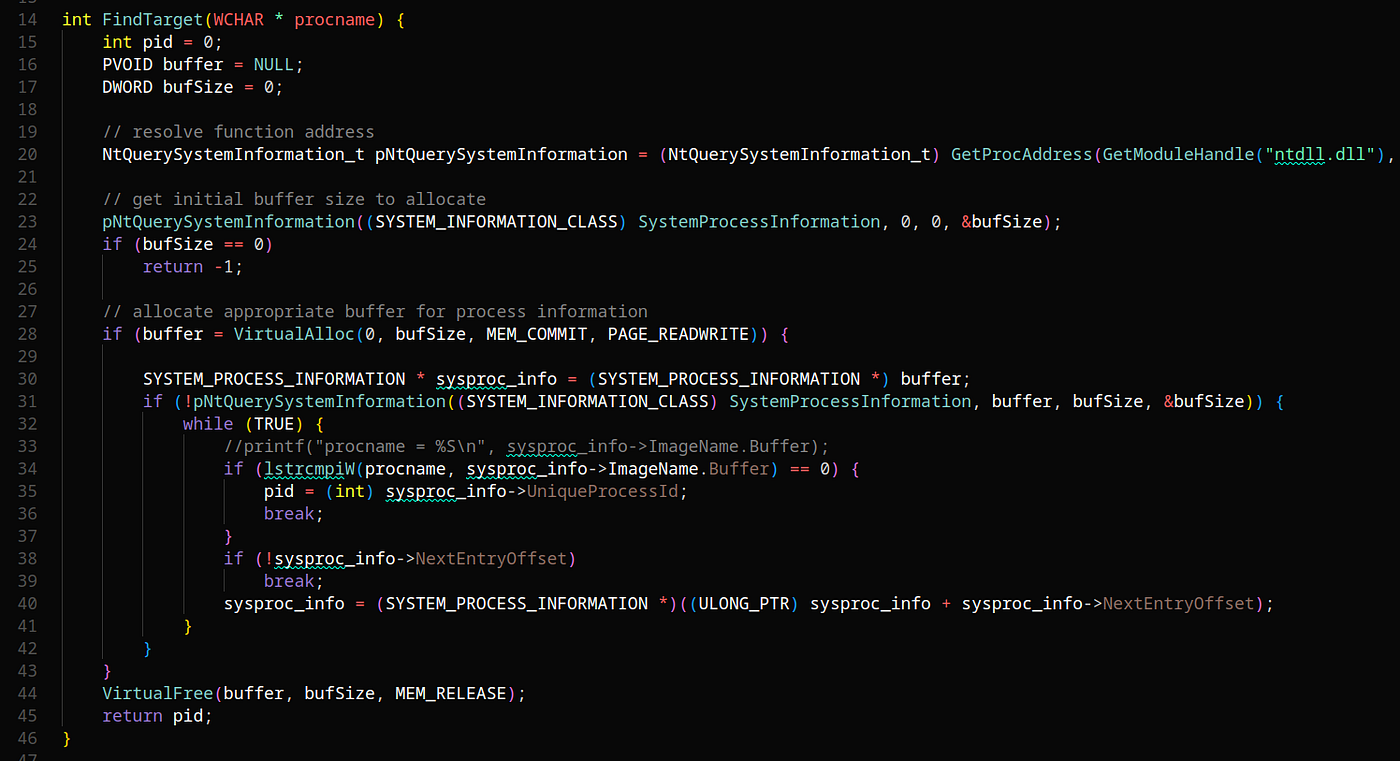
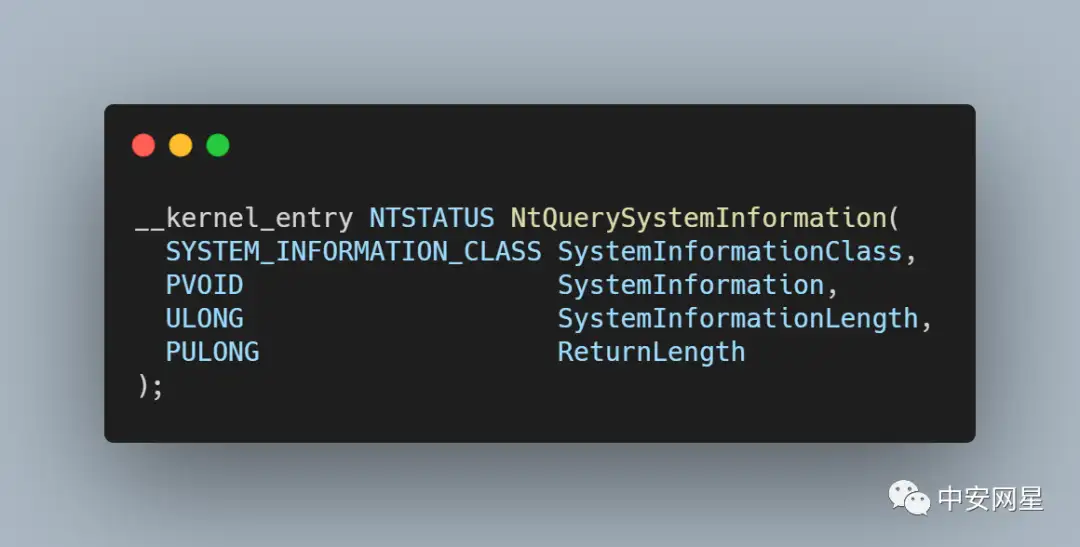
Artem I. Baranov on X: "Welcome to a new process mitigation class PS_MITIGATION_OPTION_FSCTL_SYSTEM_CALL_DISABLE (39) - EPROCESS->MitigationFlags3Values->DisallowFsctlSystemCalls; ZwSetEventEx, RtlValidateUserCallTarget and more system information ...
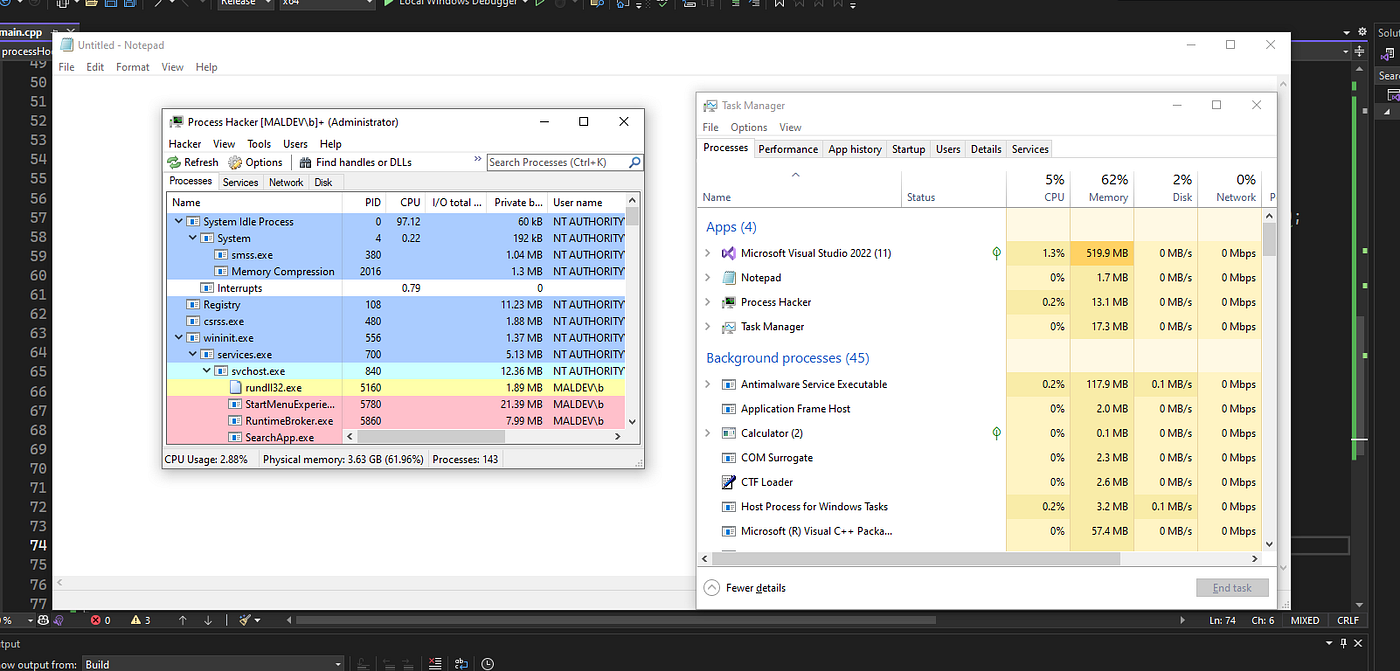
Hide Processes in Task Manager. Welcome to my new article today i will… | by S12 - H4CK | Dec, 2023 | Medium

![Upatre: Old Dog, New [Anti-Analysis] Tricks Upatre: Old Dog, New [Anti-Analysis] Tricks](https://unit42.paloaltonetworks.com/wp-content/uploads/2015/11/Upatre1.png)



![Upatre: Old Dog, New [Anti-Analysis] Tricks Upatre: Old Dog, New [Anti-Analysis] Tricks](https://unit42.paloaltonetworks.com/wp-content/uploads/2015/11/upatre5.png)


![原创]《逆向工程核心原理》——反调试技术-软件逆向-看雪-安全社区|安全招聘|kanxue.com 原创]《逆向工程核心原理》——反调试技术-软件逆向-看雪-安全社区|安全招聘|kanxue.com](https://bbs.kanxue.com/upload/attach/202012/857437_K5PBFT7MJ94AMJP.jpg)

![Upatre: Old Dog, New [Anti-Analysis] Tricks Upatre: Old Dog, New [Anti-Analysis] Tricks](https://unit42.paloaltonetworks.com/wp-content/uploads/2015/11/upatre7.png)